


For this article we highlight four specific areas of concern, Net Neutrality, the Cloud Act, the end of legal protections for hosts of user-generated content and the growing practice of searching people’s computers and phones. There are also several other ways that our internet rights are being infringed. For time and space reasons, we are not addressing these other concerns, which include social media surveillance by law enforcement and intelligence agencies, the failure of legislators to reform Section 702 of the Foreign Intelligence Surveillance (FISA) Act, the prosecution of minors for sexting, and the use of illegitimate copyright claims to suppress free expression.

Picture from the ACLU
The EFF explains the purpose and recent history of Net neutrality in the article Net Neutrality:
“Network neutrality—the idea that Internet service providers (ISPs) should treat all data that travels over their networks fairly, without improper discrimination in favor of particular apps, sites or services—is a principle that must be upheld to protect the future of our open Internet. It's a principle that's faced many threats over the years, such as ISPs forging packets to tamper with certain kinds of traffic or slowing down or even outright blocking protocols or applications.
In 2010, the Federal Communications Commission (FCC) attempted to combat these threats with a set of Open Internet rules. But its efforts were full of legal and practical holes. In 2014, after a legal challenge from Verizon, those rules were overturned, and the FCC set about drafting a new set of rules better suited to the challenge...As a direct result of that intense public activism and scrutiny, in 2015, the FCC produced rules that we could support—in part because, in addition to the bright line rules against blocking, throttling, and paid prioritization of Internet traffic, they included strict “forbearance” restrictions on what the FCC can do without holding another rulemaking..
Unfortunately, the FCC, led by a new Chair, repealed those hard-won rules just two years later, despite intense resistance from nonprofits, artists, tech companies large and small, libraries, even some ISPs, and millions of regular Internet users. What is worse, that repeal – via the ironically-named “Restoring Internet Freedom Order” -- ignored technical evidence submitted by EFF and others and showed a remarkable lack of understanding of how the Internet works.
Despite the new FCC’s best efforts, net neutrality isn’t dead. The 2017 repeal is being challenged in court, in Congress, and by the states…"
The ACLU called attention to the likely impact of the end of federally mandated Net Neutrality in the article Trump’s FCC Nukes Network Neutrality: What Happens Now?
“...Most internet subscribers will not see dramatic changes right away; the companies know that this is a hot-button issue and that people are mad. Consumer-facing companies are restrained not just by enforceable rules but also by social norms and users’ expectations. Internet users have grown to expect certain things about their online experience based on the history of the broadband internet before this radical departure. Companies will also be restrained by the political heat over network neutrality.
But that political heat can’t be sustained forever — there are too many other issues in this world...But social norms and people’s expectations can be shifted — especially by powerful, quasi-monopolistic companies that don’t face significant competition. What we’re likely to see is that the telecoms will behave like the airlines: They will relentlessly erode the quality of their customers’ experience, charging fees all the while, and customers will hate it but find themselves relatively powerless to fight back...
..With network neutrality protections stripped away, the telecoms will be free to discriminate in how they treat data crossing their networks. What can they discriminate based on? Basically anything they want. It could be the type of data (music, social media, video, gaming), the identity of the site that is transmitting it (giant incumbent able to pay hefty fees vs. unknown upstart), or the political content of the data. Such discrimination could take the form of slowing down disfavored data, or blocking it outright.
I don’t expect that the telecoms will be so bold as to start blocking access to liberal or conservative media sites right away — nor would doing so be their biggest immediate temptation...
...What the ISPs will be tempted to do first is to try to exploit their gatekeeper role to extract additional revenue from all ends of the internet. ... This will affect customers not only through higher costs paid by such services — an increase in monthly charges for streaming sites, for example — but also by impoverishing the choices and innovations available to them. Netflix may be able to pay off the gatekeepers, but what about an innovative new upstart competitor with superior service?…
...In short, the internet as we know it is not going to change overnight. But this terrible action by the FCC has torn down the barriers holding back the erosion of the open internet we have always known. We are not going to roll over for this catastrophic mistake, and neither should you.”

Picture from the TVP Strategy
“...March 23, 2018: President Donald Trump signed the $1.3 trillion government spending bill—which includes the CLOUD Act—into law Friday morning…It [The Cloud Act] was never reviewed or marked up by any committee in either the House or the Senate. It never received a hearing. It was robbed of a stand-alone floor vote because Congressional leadership decided, behind closed doors, to attach this un-vetted, unrelated data bill to the $1.3 trillion government spending bill. Congress has a professional responsibility to listen to the American people’s concerns, to represent their constituents, and to debate the merits and concerns of this proposal amongst themselves, and this week, they failed.
...Because of this failure, U.S. and foreign police will have new mechanisms to seize data across the globe. Because of this failure, your private emails, your online chats, your Facebook, Google, Flickr photos, your Snapchat videos, your private lives online, your moments shared digitally between only those you trust, will be open to foreign law enforcement without a warrant and with few restrictions on using and sharing your information. Because of this failure, U.S. laws will be bypassed on U.S. soil.
As we wrote before, the CLOUD Act is a far-reaching, privacy-upending piece of legislation that will:
•Enable foreign police to collect and wiretap people's communications from U.S. companies, without obtaining a U.S. warrant.
•Allow foreign nations to demand personal data stored in the United States, without prior review by a judge.
•Allow the U.S. president to enter "executive agreements" that empower police in foreign nations that have weaker privacy laws than the United States to seize data in the United States while ignoring U.S. privacy laws.
•Allow foreign police to collect someone's data without notifying them about it.
•Empower U.S. police to grab any data, regardless if it's a U.S. person's or not, no matter where it is stored.”
ACLU Legislative Counsel Neema Singh Guliani’s article expands on the threats to privacy allowed by the Cloud Act:
“Despite its fluffy sounding name, the recently introduced CLOUD Act is far from harmless. It threatens activists abroad, individuals here in the U.S., and would empower Attorney General Sessions in new disturbing ways…Today, the information of global activists — such as those that fight for LGBTQ rights, defend religious freedom, or advocate for gender equality are protected from being disclosed by U.S. companies to governments who may seek to do them harm. The CLOUD Act eliminates many of these protections and replaces them with vague assurances, weak standards, and largely unenforceable restrictions.
The bill starts by giving the executive branch dramatically more power than it has today. It would allow Attorney General Sessions to enter into agreements with foreign governments that bypass current law, without any approval from Congress. Under these agreements, foreign governments would be able to get emails and other electronic information without any additional scrutiny by a U.S. judge or official. And, while the attorney general would need to consider a country’s human rights record, he is not prohibited from entering into an agreement with a country that has committed human rights abuses.
That level of discretion alone is concerning. Even more, however, the bill would for the first time allow these foreign governments to wiretap in the U.S. — even in cases where they do not meet Wiretap Act standards. Paradoxically, that would give foreign governments the power to engage in surveillance — which could sweep in the information of Americans communicating with foreigners — that the U.S. itself would not be able to engage in. The bill also provides broad discretion to funnel this information back to the U.S., circumventing the Fourth Amendment. This information could potentially be used by the U.S. to engage in a variety of law enforcement actions.
On top of this, the bill does not require that the Department of Justice or any U.S. government entity review individual requests for information made by foreign governments to ensure that human rights are not being violated...”
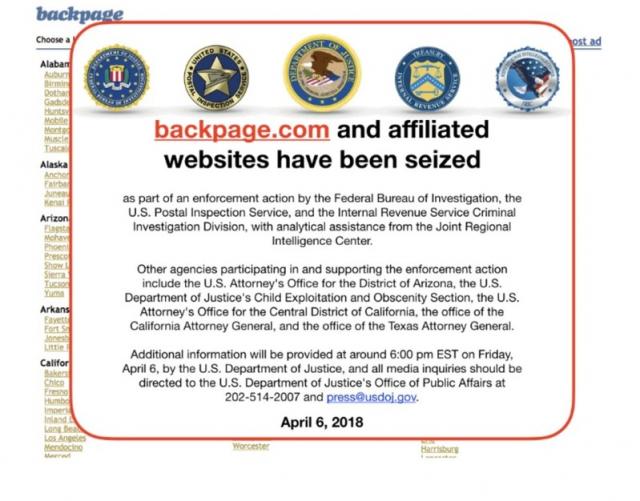
In the guise of preventing sex trafficking the bills known as FOSTA (Fight Online Sex Trafficking Act) or SESTA (Stop Enabling Sex Traffickers Act), make hosts of online community forums, classified advertisers, and user-generated content (ie. YouTube, Instragram) subject to potential criminal prosecution for content created and posted by a member of the public. This law has already had a chilling effect on free speech. One of the most visible examples was Craigslist's decision to eliminate all of its personal adverts for people offering or seeking friendship, love or sex.
The EFF summarized its concerns on the Stop SESTA web page:
“The “Stop Enabling Sex Traffickers Act” or SESTA may be well intentioned, but it aims at the wrong target. Instead of focusing on finding and punishing sex traffickers, this bill focuses on Internet platforms and restricting speech online.
SESTA impacts any platform that hosts user-generatedcontent by rolling back Section 230 protections. Websites and apps we all use every day –from WhatsApp and Instagram to Yelp and Wikipedia, even bloggers with comments sections –rely on this protection. Under the current system, users are generally liable for the content they post, not the platforms. If SESTA passes, these platforms will be exposed to significantly more liability for what their users do with their services. That will create an incentive to review anything a user wants to post, if the platform decided to allow user content at all.
Section 230 can be credited with creating today’s Internet. It provided the legal buffer entrepreneurs needed to experiment with new ways to connect people online and is just as critical for today’s startups as it was for today’s popular platforms when they launched.”
Ian Thompson, Legislative Representative for the ACLU reveals how this law creates more risk of harm for sex workers and does little to prevent genuine sex trafficking in the article Congress Proposes to Fight Online Trafficking By Harming Sex Workers.
“...the legislation known as the Fight Online Sex Trafficking Act, or FOSTA, could harm the very people that it is intended to protect. The legislation also threatens the vibrancy of the internet as the world’s most significant marketplace of ideas, and it will inhibit its growth as a place of creativity and innovation.
Proposals to address sex trafficking should not make workers in the sex trade more susceptible to violence and exploitation. FOSTA threatens the lives and safety of sex workers — people who are disproportionately LGBTQ and people of color. The legislation does this through a dangerously broad definition of “promotion of prostitution,” which is not limited to trafficking and could sweep in any trading of sex for money or other goods. The bill also creates a new, vaguely defined federal crime for the facilitation of prostitution which could result in a prison sentence of up to 10 years. FOSTA’s definition of “facilitation” is so open to interpretation that it could include critical harm reduction and anti-violence tactics that sex workers depend on to survive.
These harm reduction tactics include being able to share information and techniques online, such as screening clients for violence; online advertising, which allows people to work in safer locations off the street and to be more discerning about clients; and “Bad Date Lists,” which host information online about individuals who have previously victimized those who trade sex.
Taking away the ability of sex workers to utilize online platforms to meet clients will force them back into street-based work where there is less time to negotiate safety needs and a higher risk of violence from both clients and law enforcement. An important 2017 study from West Virginia University and Baylor University found a 17 percent drop in rates of homicide against women correlated to Craigslist opening its Erotic section because it made sex work safer...The ability to access online platforms to advertise means that sex workers are able to screen clients for safety, negotiate boundaries such as condom use, and work in physically safer spaces.
FOSTA threatens to take these essential survival tools away from sex workers. Doing so will not help victims of trafficking, but it will endanger some of the most vulnerable members of our communities….”
In Vox.com, Aja Romano reports on the impact of the new law in the article A new law intended to curb sex trafficking threatens the future of the internet as we know it.
"Wondering why Craigslist recently killed its (in)famous Personals section? You can thank Congress — and you can start bracing for more deletions and censorship to come.
This week, President Trump signed into law a set of controversial bills intended to make it easier to cut down on illegal sex trafficking online. Both bills — the House bill known as FOSTA, the Fight Online Sex Trafficking Act, and the Senate bill, SESTA, the Stop Enabling Sex-Trafficking Act — have been hailed by advocates as a victory for sex trafficking victims.
But the bills also poke a huge hole in a famous and longstanding “safe harbor” rule of the internet: Section 230 of the 1996 Communications Decency Act. Usually shorthanded as “Section 230” and generally seen as one of the most important pieces of internet legislation ever created, it holds that “No provider or user of an interactive computer service shall be treated as the publisher or speaker of any information provided by another information content provider.” In other words, Section 230 has allowed the internet to thrive on user-generated content without holding platforms and ISPs responsible for whatever those users might create…
In the immediate aftermath of SESTA’s passage on March 21, 2018, numerous websites took action to censor or ban parts of their platforms in response — not because those parts of the sites actually were promoting ads for prostitutes, but because policing them against the outside possibility that they might was just too hard.
...Two days after SESTA’s passage by the Senate, Craigslist removed its entire personals section from its platform, citing the difficulty of adhering to the new changes to the law if it continued to allow open posting on its dating section. The move left Craigslist users quizzing one another for alternative personals sites, and sent some into the “activity” category with wink-wink requests for “activity partners.”
...The furry-centric dating website Pounced.org was another casualty of the bill combo. When it shut down overnight a week after SESTA passed, the website left a lengthy note explaining that specific language in FOSTA undermined Section 230 in a way that made 'sites operated by small organizations like pounced.org much riskier to operate.'
'We don’t promote prostitution or sex trafficking,” the site’s moderators wrote. “We’re a personals site for the furry community...The problem is, with limited resources and a small volunteer staff, our risk for operating the site has now significantly increased.'
...Similarly, in late March, Microsoft abruptly announced a drastic change to its policies and enforcement of those policies that effectively scoured its many services, including Skype and its cloud storage products, of any adult content. This drew complaints from Skype users, who feared that Microsoft’s auto-detection filters would ban any Skype user who happened to be involved in consensual sexual activity using the platform."

Picture from the ACLU
In recent years, the federal government began doing warrantless, and often suspicionless, searching and copying of the content of traveler’s computers, phones and other devices at the border. Some travelers have been forced to provide border patrol agents with the passwords for their social media accounts, e-mail and devices. There have also been incidents of warrantless and suspicionless searches of devices by police unrelated to border crossing.
Esha Bhandari, Staff Attorney, ACLU Speech, Privacy, and Technology explains the situation in the article The Government’s New Policy on Device Searches at the Border: What You Need to Know in January 2018.
“The government last week issued new rules governing its searches of electronic devices at the border on the same day that it revealed that such searches skyrocketed in 2017.
Until now, Customs and Border Protection claimed the authority to demand travelers turn over their phones, laptops, and other devices to be searched at border crossings, including airports, without any suspicion of wrongdoing. The new directive released Friday will require a heightened level of suspicion for certain searches, but it reasserts CBP’s authority to conduct other searches without any level of individualized suspicion whatsoever.
According to data released by the Department of Homeland Security, searches of electronic devices rose by about 60 percent in 2017 relative to 2016. A lawsuit we filed last year along with the Electronic Frontier Foundation challenges these warrantless searches as unconstitutional on behalf of 11 travelers who were subjected to them.
The new CBP policy indicates that officers at the border should have reasonable suspicion of unlawful activity or a “national security concern” before they can conduct an “advanced” search of the contents of an electronic device. An advanced search — sometimes called a forensic search — is any search involving external equipment connected to an electronic device to scan, analyze, or download the data on the device. The CBP directive also reaffirms that officers cannot search information located remotely — in the cloud, for example — and that they should place devices in airplane mode to avoid seeing such material. However, “basic searches” conducted on the spot — which can expose travelers’ photographs, contact lists, text messages, emails, and documents — can continue without individualized suspicion under the new directive.
This directive is a welcome development because it at least acknowledges the severe privacy invasions that occur when the government can search your device without any suspicion. Indeed, recently published accounts of complaints filed with the federal government powerfully illustrate the humiliation individuals have experienced when forced to surrender their personal devices to the scrutiny of border officers.
That said, the directive doesn’t go nearly far enough.
We have long argued that the Constitution requires the government to get a warrant before searching electronic devices at the border, and we support bipartisan legislation that would make that requirement law. The CBP directive only requires reasonable suspicion, a lower legal standard than the probable cause standard needed for a warrant, and it doesn’t require agents to make a case before a judge.
The new directive still requires no suspicion at all when an advanced search implicates a “national security concern” — which is not clearly defined in the policy and is potentially vague enough to cover a wide array of scenarios — or when a search is not considered advanced. But even so-called “basic” searches can be incredibly invasive, exposing the intimate details of a person’s life to government agents who never have to make a case for why they need to conduct the search.
Additionally, the directive does not apply to agencies outside of CBP that might conduct searches of devices taken at the border, and does not make clear that travelers should not be under an obligation to provide border officers with a password or other information to enable them to search their device.”
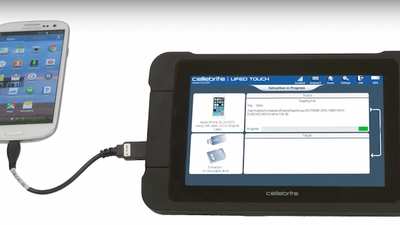
Picture from the Motherboard.
The government now has access to tools that make it easier to clone (copy) and search your phone. The threat to privacy and how it can be contained is examined in Mobile-Phone Cloning Tools Need to Be Subject to Oversight — and the Constitution by Jay Stanley, Senior Policy Analyst, ACLU Speech, Privacy, and Technology Project
“The claim by U.S. border officials that they can, with no grounds for suspicion, look through and copy travelers’ cell phones and other electronic devices is creating justified consternation. But it’s important to realize that police are also doing such searches domestically, sometimes without a warrant. Whether at the border or internally, the technology that is often used for those searches is called “mobile forensic data extraction devices”—portable machines that can download exact copies of a phone's entire memory. A company called Cellebrite is the most prominent maker of these devices; its products are sometimes described as the most advanced, and they are in wide use across U.S. law enforcement agencies.
This is an enormously powerful technology, and it needs to be subject to careful checks and balances. The use of these devices is already regulated by the Constitution, but additional protections ought to be enacted, ranging from tight internal law enforcement controls to prevent abuse, to close legislative monitoring and, if appropriate, regulation of law enforcement use.
The technology
Cellebrite and other mobile forensic extraction devices allow access to an enormously broad and intrusive range of data from cell phones. That information can include:
•Call activity
•Phone book directory information
•Stored voicemails and text messages
•Photos and videos
•Apps
•Passwords
•Geolocation history, including cell towers and WiFi networks with which the cell phone has previously connected.
Cellebrite boasts that its devices can download “hidden, and deleted phone data” including “call history, text messages, contacts, images, and geotags.”
These devices also claim decryption capabilities. We don’t know their precise limits, but it is safe to assume that the more advanced versions for sale have a state-of-the-art ability to break anything that it is poorly encrypted, where passwords are not strong (such as pins), or where software bugs not known to the public (so-called “zero-days”) may allow it.
Furthermore, a Cellebrite product called “UFED Cloud Analyzer” allows police to access not only the information on a phone, but also all the information stored on cloud services, “utilizing login information extracted from the mobile device.”…
...Domestic cell phone searches should never be performed without a warrant based on probable cause. There is no difference between searching a cell phone and searching a personal computer, and the latter always requires a warrant. The Supreme Court has already ruled (in Riley v. California) that despite longstanding rules allowing police searches incident to arrest, the police may not search cell phones incident to arrest without a warrant because of the unprecedented amount of information now held on modern phones.
We have received reports that police in some places are routinely using Cellebrite without a warrant under the justification that the threat of remote wiping of seized phones constitutes an “exigent circumstance.” This rationale does not hold water and was expressly rejected by the Supreme Court in Riley...
...Like search warrants for desktop or laptop computers, any warrant to access a phone should particularly and narrowly describe the data that law enforcement have probable cause to believe is related to a crime. Just like a warrant for a person’s business records in a fraud case shouldn’t authorize police to look through their family photographs or medicine cabinet, a warrant looking for text exchanges with a particular number shouldn’t allow police to look through photos or financial information stored on your phone, or in the cloud.
Nor should access through a phone to data stored in the cloud be carried out without specific, explicit authorization in a warrant.
Other points:
•Searches should not be based on the fiction that consent from a citizen is “voluntary”—that individuals are free to refuse to cooperate with police officers asking to clone their cell phone data. Police officers have significant power and discretion in their encounters with civilians and few such police requests will be uncolored by coercion. Officers should be directed by policy not to make such requests.
•Police should be open and transparent about their usage of and policies and practices with regard to this technology.
•Some have proposed state laws creating an “implied consent” for cellphone searches in the aftermath of a serious automobile accident, so that the authorities can check whether use of a phone while driving contributed to an accident. This was proposed in the 2016 session in New York state as something called “Evan’s Law,” though the legislature did not pass it. The existing warrant framework is the proper way to approach such situations, and the ACLU opposes such laws….”
![]() Back to Oranj Productions Home
Page
Back to Oranj Productions Home
Page
Contact Info
All content Copyright 1993-2018 Oranj Productions.
All Rights Reserved.